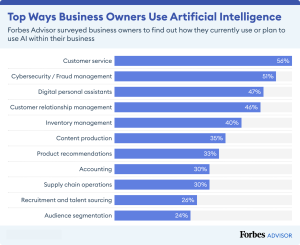
Artificial Intelligence (AI) has become a cornerstone of modern business, driving productivity, efficiency, and enhancing customer experiences. Let’s delve into how AI can transform key business domains: Customer Experience (CX), Cybersecurity, Cloud, and the Internet of Things (IoT).
Enhancing Customer Experience (CX)
Generative AI is set to revolutionize customer experience (CX) by transforming how businesses interact with their customers and optimize operations. According to Metrigy’s AI for Business Success 2024-25 survey, 39% of IT, CX, and business leaders believe 2024 will mark a significant shift toward adopting AI for customer interactions, with another 20% anticipating this change in 2025. For businesses already leveraging AI in CX, the benefits are extensive, ranging from predictive and responsive services to significantly improved customer satisfaction and operational efficiency.

Personalization
Mastering personalization at scale is crucial for boosting customer engagement. AI enables businesses to deliver highly tailored experiences, from individualized product recommendations to personalized communication strategies. Research shows that marketers leveraging ultra-tailored personalization report significantly higher ROI compared to those who don’t. Imagine a retail store using AI to analyze customer data, allowing for personalized email campaigns that recommend products based on individual preferences and sizes.
Omnichannel Engagement
AI is making seamless omnichannel customer experiences more achievable than ever. Customers now expect consistent interactions across various touchpoints, whether through text, web, social media, or email. In healthcare, for instance, AI can facilitate smooth appointment scheduling via chatbots and provide proactive treatment reminders, enhancing patient experience and adherence to treatment plans. This not only improves patient satisfaction but also optimizes operational efficiency for healthcare providers.
Emotional AI
Emotional AI enhances customer service by fostering deeper emotional connections between customers and brands. Sentiment analysis, personalized interactions, real-time feedback, and predictive analytics help businesses understand and respond to customer emotions effectively. For example, a banking app with an AI chatbot can predict customer stress related to potential fraud and proactively offer reassurance, building trust and satisfaction.
Strengthening Cybersecurity
As cyber threats become more complex, AI is crucial in enhancing threat mitigation strategies. Cyberattacks have grown in sophistication, and now AI hacking tools are becoming accessible online, increasing the number of less skilled cybercriminals who can launch attacks. Deep Instinct’s 2023 Voice of SecOps Report highlights that 75% of security professionals observed a rise in attacks over the past year, with 85% blaming the surge on the use of generative AI by malicious actors.
The message is clear: Organizations must prioritize and continuously update their advanced security measures to address threat detection and fraud prevention. The stakes are high, as IBM’s 2023 Cost of a Data Breach Report indicates that the average breach costs over $4 million in lost business and fines. Alarmingly, 35% of US companies still lack dedicated cybersecurity personnel.

Threat Detection
AI-powered systems utilize machine learning algorithms to monitor network traffic and identify potential cyberattacks. By analyzing patterns and adapting to new threats, businesses can strengthen their security posture and protect valuable data.
Fraud Prevention
AI algorithms excel at detecting fraudulent activity by analyzing transaction data for anomalies. Financial institutions, for example, can use AI to flag suspicious transactions, minimizing financial losses and enhancing customer protection.
Zero-Trust Security
The zero-trust model, based on the principle of “never trust, always verify,” emphasizes continuous verification of users and devices. This approach is essential for securing data in today’s digital landscape, where traditional perimeter security is no longer sufficient.
Two-Factor Authentication
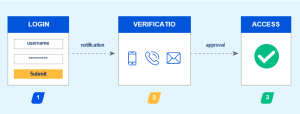
Optimizing Cloud Operations
Gartner projects public spending on cloud tools and services to hit $679 billion in 2024 and soar to $1 trillion by 2027. A significant portion of this investment will be fueled by the rising demand for new AI-powered platforms and as-a-service offerings. AI models, like the large language models (LLMs) behind tools such as ChatGPT, require extensive data and substantial compute power for training. Many businesses lack the resources or infrastructure to manage this independently. However, by utilizing AI-as-a-service through cloud-native platforms, they can harness real-time data collection and analysis to fully leverage AI capabilities.

Resource Optimization
AI-driven cloud management platforms dynamically allocate resources based on demand, ensuring optimal performance and cost-efficiency. This automatic scaling minimizes downtime and reduces infrastructure costs.
Predictive Maintenance
AI analytics predict equipment failures and schedule maintenance proactively, preventing downtime. For instance, manufacturing companies can use AI to analyze sensor data and identify signs of impending machinery malfunctions, ensuring smooth operations.
Robotic Process Automation (RPA)
Cloud-based RPA enables businesses to automate processes more efficiently than traditional on-premises solutions. For example, a finance team can automate invoice processing using AI and OCR technology, enhancing scalability and reducing manual intervention.

Revolutionizing IoT and Predictive Analytics
The Internet of Things (IoT) is becoming increasingly prevalent, from self-driving cars to wearable health devices. By 2025, IoT devices are predicted to outnumber non-IoT devices by a ratio of 3:1. While IoT forms the skeletal framework of interconnected devices that collect and exchange data, AI serves as the brain, analyzing and interpreting this data to make intelligent decisions autonomously. The fusion of AI and IoT, known as AIoT, creates a smarter, self-improving network of devices that not only gather data but also learn from it, optimizing processes and generating greater value.
As IoT devices and the volume of data they process continue to grow, so do the business opportunities for AIoT. However, the main challenge for business leaders is to utilize this data effectively. Gartner reports that 87% of organizations have limited business intelligence and analytics maturity, which means many businesses underutilize their data and fail to derive value from it. By integrating AI-based solutions and partnering with AIoT service providers, companies can maximize their IoT investments, achieving greater efficiency and cost savings.

Computer Vision for Physical Security
AI integrated with IoT cameras and sensors can monitor and protect physical environments. AI systems can analyze video feeds to detect threats such as unauthorized access, fire, or safety hazards, allowing for timely responses and increased security.
Predictive AI for Home-Based Healthcare
Wearable IoT devices collect patient health data, while AI analyzes this data to predict potential health issues, enabling proactive care. This predictive capability is crucial for improving patient outcomes and reducing healthcare costs.
Energy Efficiency in Building Management
IoT sensors in smart buildings monitor energy usage, and AI algorithms optimize resource consumption. For example, AI can adjust heating and lighting based on occupancy and natural light levels, reducing utility bills and the building’s carbon footprint.

Conclusion
AI’s integration across Customer Experience, Cybersecurity, Cloud, and IoT is revolutionizing how businesses operate. By leveraging AI, companies can enhance efficiency, secure their operations, and drive innovation. The business value of AI is undeniable, and its strategic implementation is essential for maintaining a competitive edge in today’s market.
At BrainCloud Group, we specialize in helping businesses unlock the full potential of AI. If you’re ready to explore how AI can transform your operations, contact us: info@braincloudgroup.com




















